Single Sign On via SAML in Microsoft Azure
Please note: Limited 3
The option to use SAML in your edoobox account is available with the Limited 3 subscription and above. Free support for this topic is limited. If you require more extensive support, we are happy to offer you paid services.
The implementation of a SAML-based single sign-on (SSO) solution in edoobox enables users (super admins, admins, and managers) to navigate seamlessly and securely between their identity provider (Microsoft Azure) and edoobox without having to log in to edoobox again each time or use a new password. This integration helps save time and increase the security of user accounts.
What is SAML?
SAML (Security Assertion Markup Language) Identity Provider (IdP) is a security service that allows users to log in to multiple applications with a single username and password. The IdP generates secure login credentials (SAML assertions) and sends them to the service providers (SP) that host the applications the user wants to log in to. The IdP handles user authentication and authorization, while the SP processes the user's login credentials and controls access to the applications.
1. Create an enterprise application in Azure AD
Create a new enterprise application in Azure AD. To do this, go to the Azure portal and select "Enterprise applications." Click on "Create your own application" and enter a name for the application (e.g., edoobox SSO).
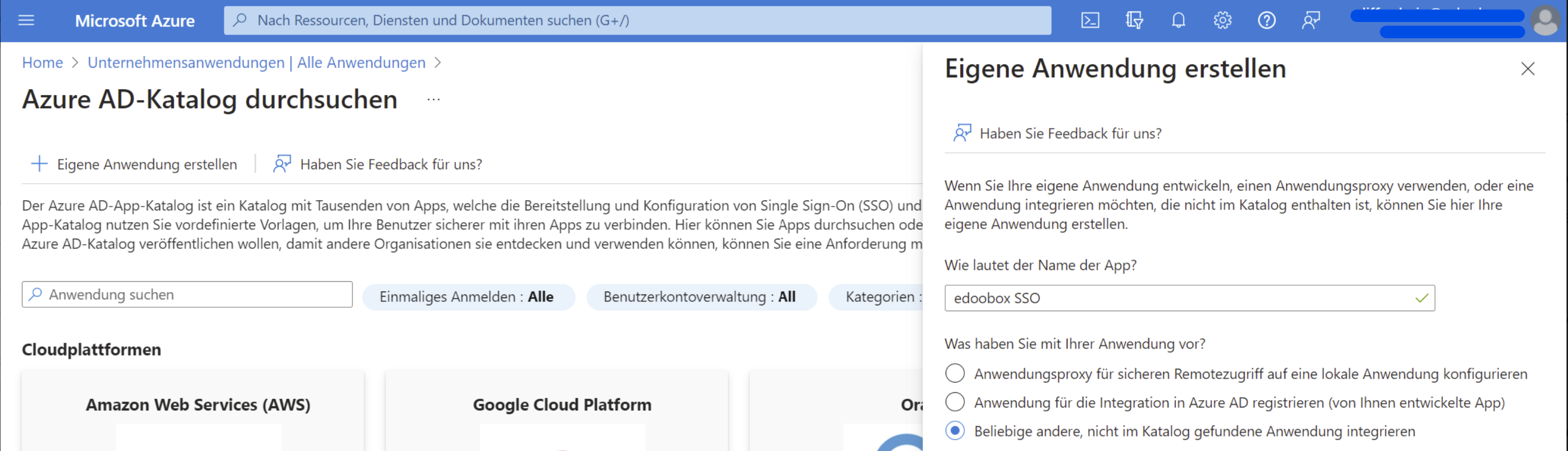
Create your own application: Set up an enterprise application in Azure AD
2. Configure the app
Configure the settings in the "Single Sign-On" menu. Select the SAML method and enter the following values:
Reply URL: Enter the value "https://app2.edoobox.com/v2/auth/saml/reply".
Identifier (Entity ID): Defined in step 5
Creation of the entity ID for use as a remote XML URL
Optimize the app settings as needed. Here you can configure the registration guidelines or define custom attributes, among other things.
Optional: Add additional attributes:
If an email address already exists, you have the option to merge the new user with the existing user or create a new user with a different email address.
"allow_migration_user": trueAre you planning to pass the ACL (recommended)? If so, please refer to optional steps 3 and 4 of these instructions and set the value here to "true."
"allow_permission_acl": true
If you do not want to integrate ACL, skip to c. and proceed directly to step 5 (enable/activate SSO via edoobox).If an active SAML connection exists, the classic edoobox login can be deactivated.
"allow_edoobox_login_when_connected: true
Info: What is edoobox ACL?
edoobox ACL (Access Control List) can be used for user authorization management, and each user group can be assigned a value from an edoobox right. If you do not use edoobox ACL, the admin with the same email address and authorization must be manually entered in edoobox before the user can log in via SSO.
3. Define edoobox ACL user rights groups (optional)
We generally recommend using edoobox ACL to control access permissions. To enable us to obtain the permissions from your Azure AD, enter a new "claim" under "Attributes" with the name: "edoobox.acl" and the source attribute "user.assignedroles."
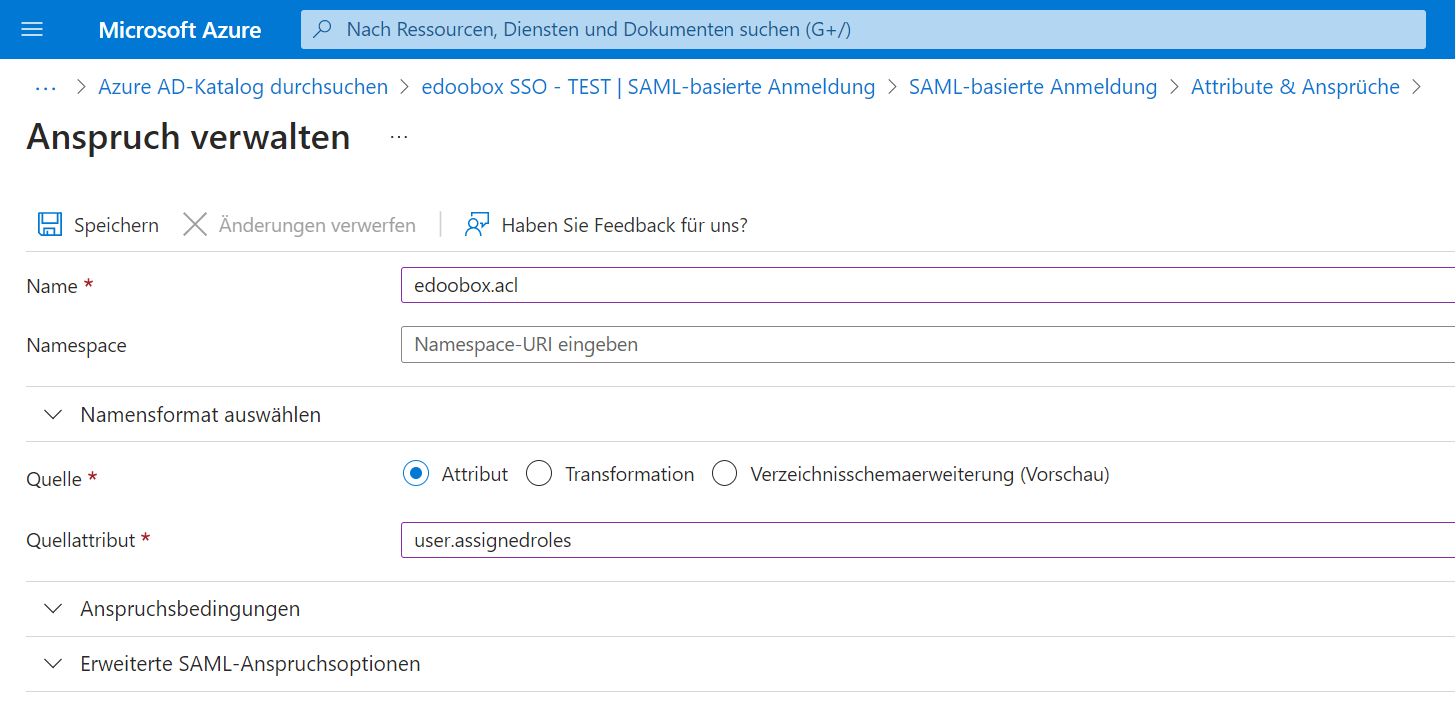
Manage entitlement: Record user rights groups as attributes
To assign app roles (edoobox.acl) in Azure, follow these steps:
Select "App roles" from the menu on the left. If this menu item is not visible, select "Users and groups" from the menu and click on the "Application registration" link, which will take you to the page where you can define the app roles.
Create a new role by clicking on the "Create new role" button.
Enter an ad name and the value for the role, then save the 5 roles.
Value: Display nameedoobox.acl.0: No rightsedoobox.acl.1: User (No rights)edoobox.acl.2: Headedoobox.acl.3: Administratoredoobox.acl.4: Super admin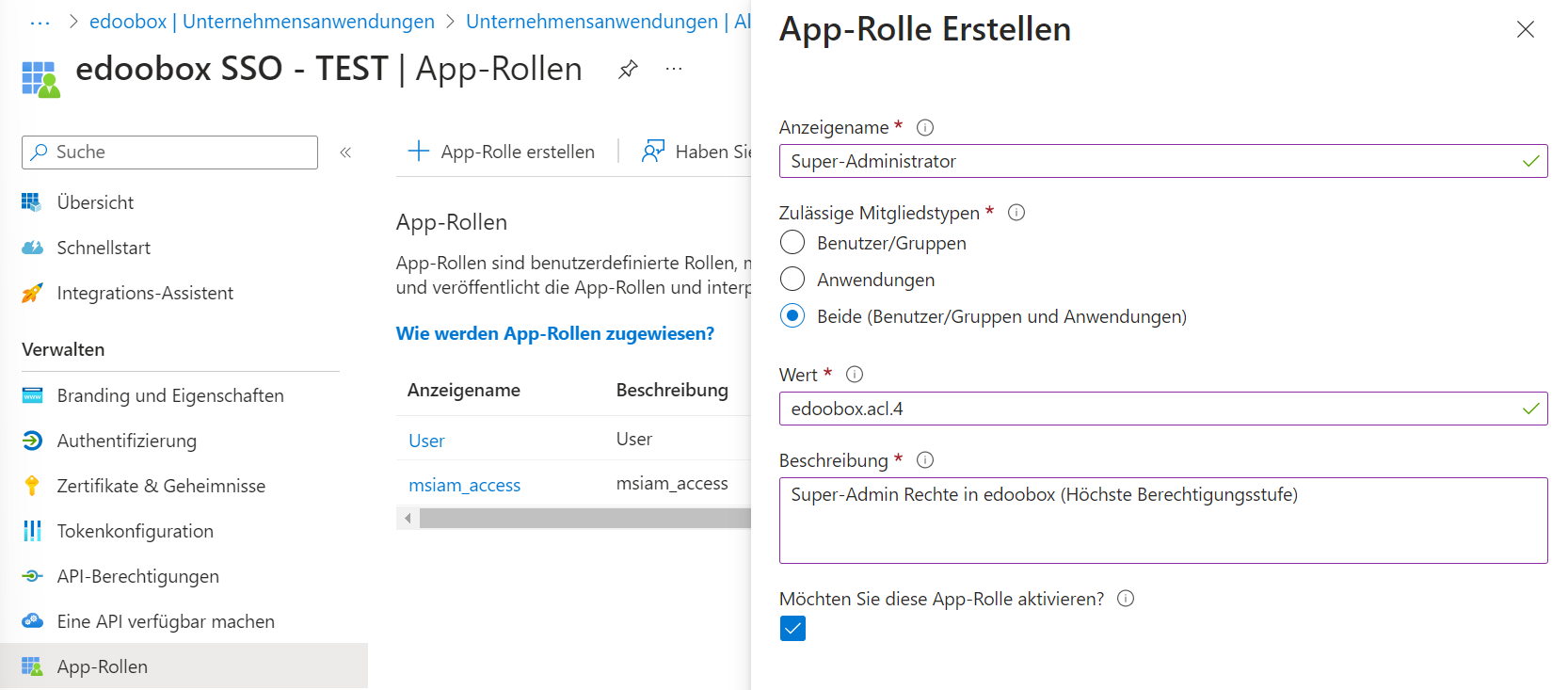
Create app role: Create edoobox roles in Azure
4. Assign edoobox ACL rights to groups and users (optional)
Then navigate back to the Azure portal, select the "Enterprise applications" you created, and select "Users and groups" in the left-hand menu.
Click on the "Add user/group" button.
Enter the required information for the user or group object, such as the name, email address, or group name.
Add users or groups to your enterprise application by assigning the users or groups.
Select the role you want to assign to the user or group and click "Assign."
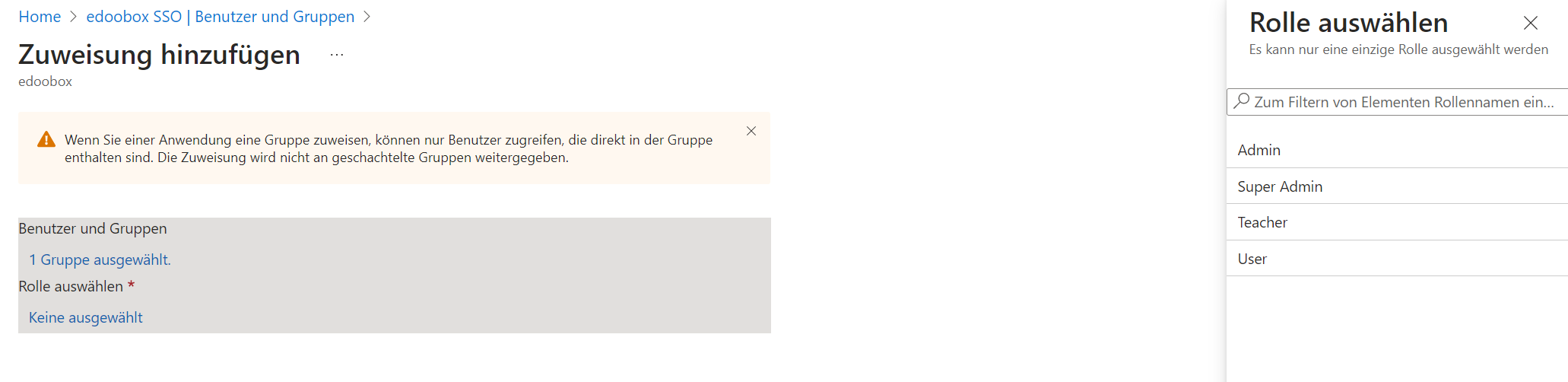
Select role: Assign groups to the created rights
5. Activate SSO in edoobox
The following documentation explains exactly how to activate this feature: Activating single sign-on via SAML in edoobox
6. Activation of SSO
Check whether the login works by logging in at the following URLs:
edoobox V1 login URL: https://app2.edoobox.com/login/sso/IHR-EDOOBOX-KÜRZEL/
edoobox V2 login URL: https://app2.edoobox.com/ed-admin/pages/sso/IHR-EDOOBOX-KÜRZEL/
Note: Redirect to SSO
If an administrator is logged in with SSO and logs out or is automatically logged out by edoobox, the logged-out administrator is automatically redirected to the SSO login page and not to the normal login page. For this to work, the administrator must have logged in at least once before.
Related instructions
Keywords for these instructions
SSO ¦ SAML ¦ Enterprise Application ¦ Azure AD
