Activate Single Sign On via SAML in edoobox
Please note: Limited 3
The option to use SAML in your edoobox account is available with the Limited 3 subscription and above. Free support for this topic is limited. If you require more extensive support, we are happy to offer you paid services.
The implementation of a SAML-based single sign-on (SSO) solution in edoobox enables users (super admins, admins, and managers) to navigate seamlessly and securely between their identity provider (Microsoft Azure) and edoobox without having to log in to edoobox again each time or use a new password. This integration helps save time and increase the security of user accounts.
What is SAML?
SAML (Security Assertion Markup Language) Identity Provider (IdP) is a security service that allows users to log in to multiple applications with a single username and password. The IdP generates secure login credentials (SAML assertions) and sends them to the service providers (SP) that host the applications the user wants to log in to. The IdP handles user authentication and authorization, while the SP processes the user's login credentials and controls access to the applications.
Activation of SSO
In the edoobox settings under SAML (SSO), you have the option to add a provider A.
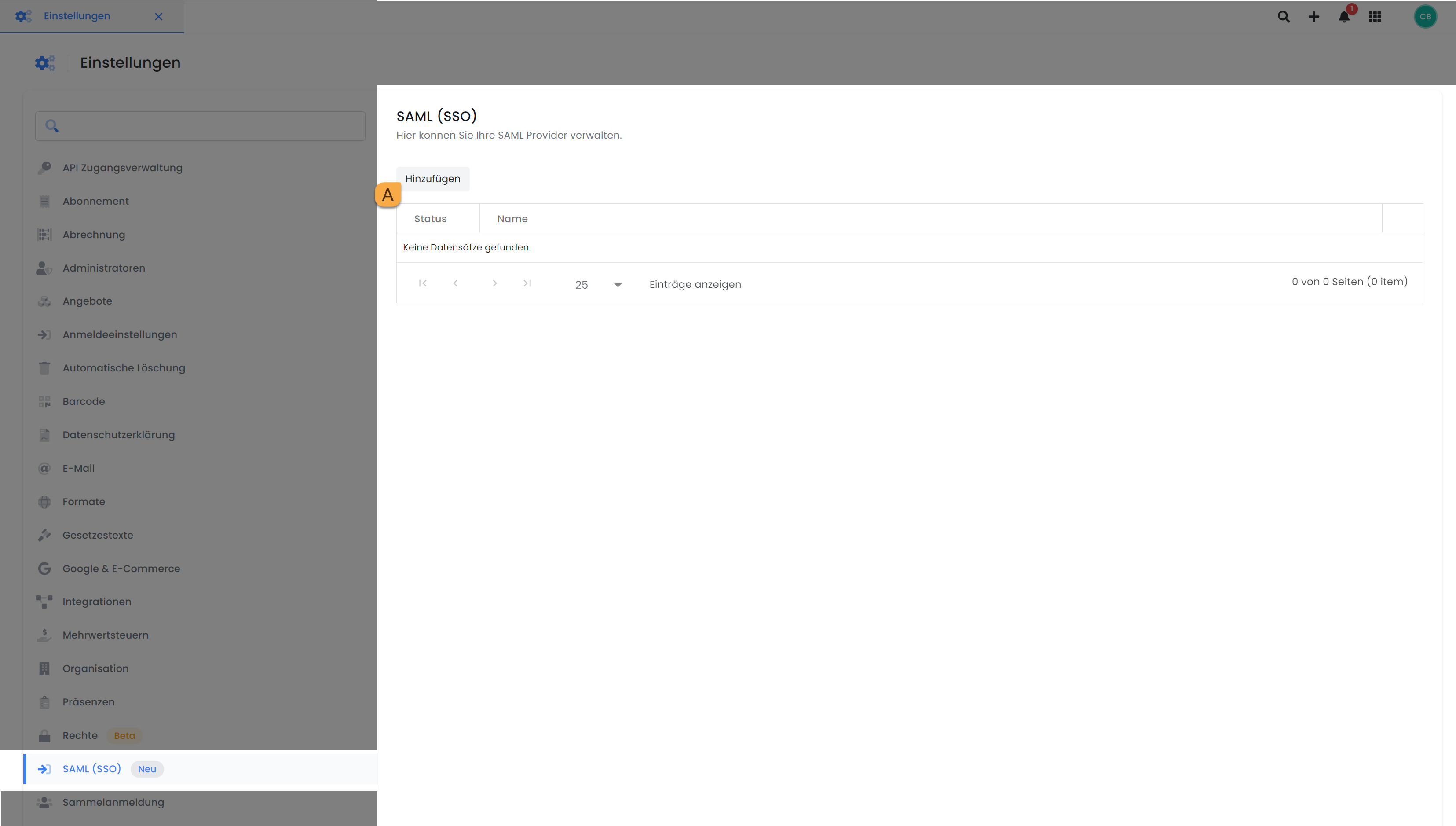
SAML (SSO) settings: SAML provider management
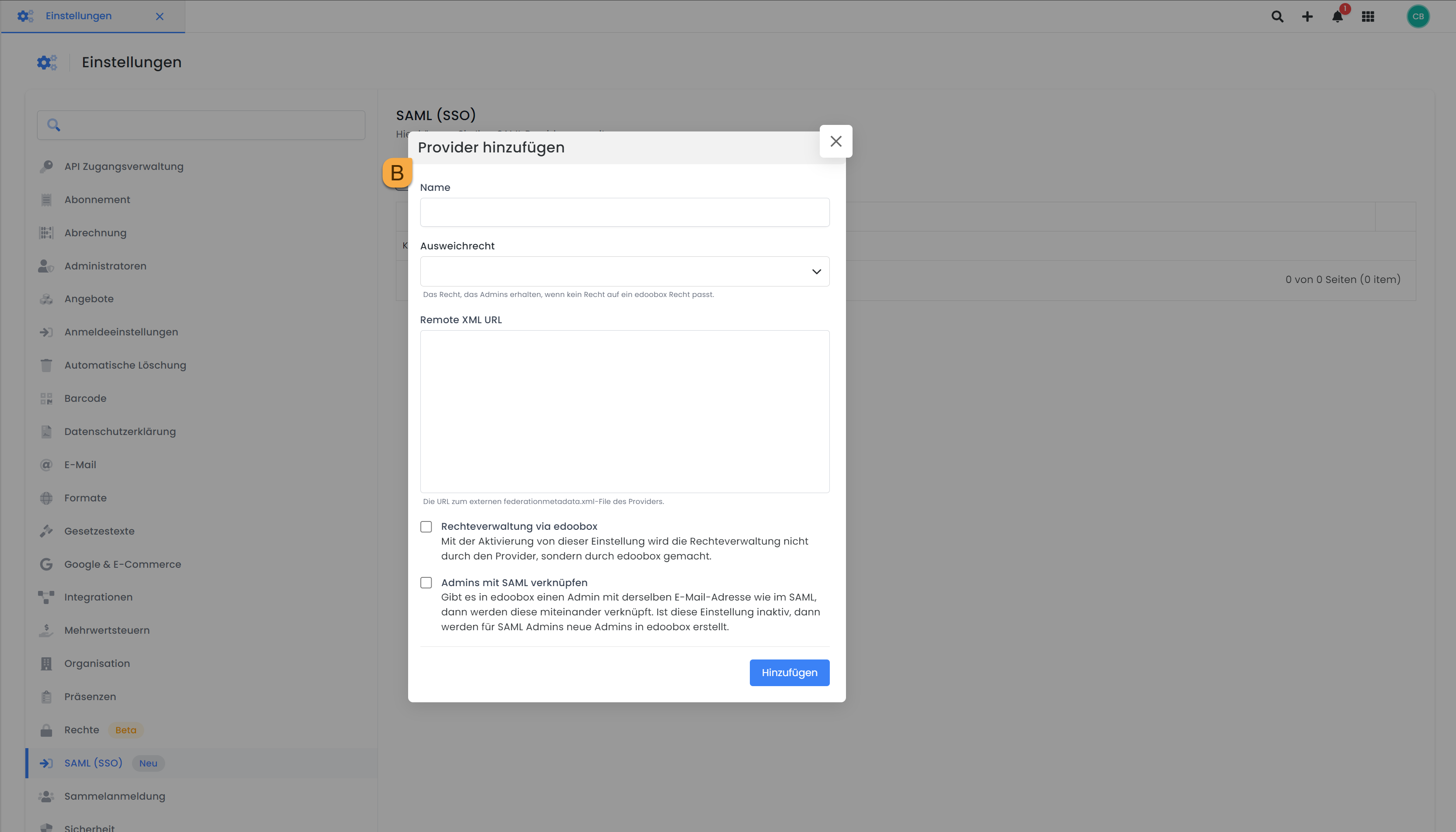
SAML (SSO): Add provider
Add Provider B
Name
The name used to label the login button could be "SSO your company name," for example. This name serves as a clear indication to users that the button is used for single sign-on (SSO) with your company identity. This name can be changed at any time.
rights of way
If you do not want to control rights management via the authentication provider (Auth Provider), you can set the default right to no rights RECOMMENDATION. This means that rights are not automatically assigned by the authentication service, but are configured by edoobox.
Remote XML URL
For Remote XML URL, you must store the provider's external federationmetadata.xml file. You can find the APP Federation Metadata URL in your Microsoft Azure account.
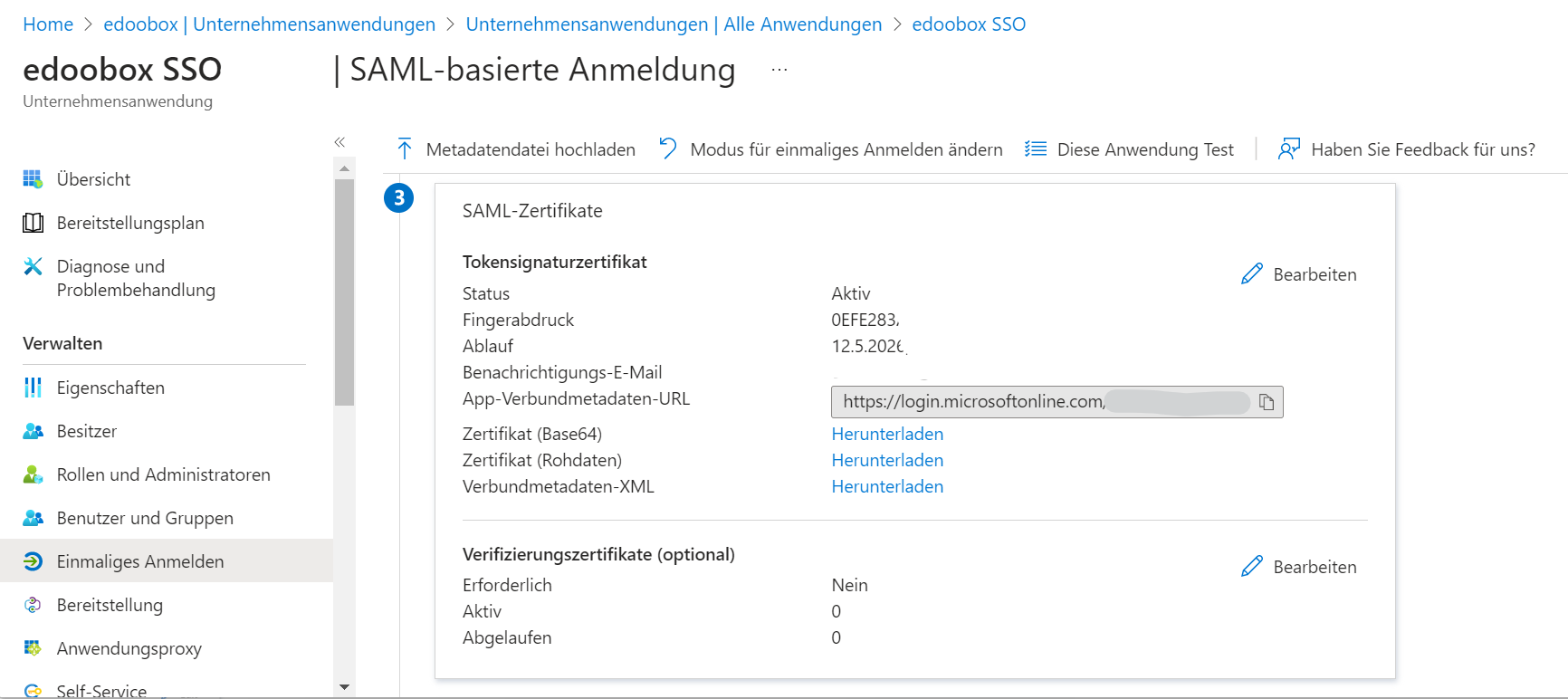
SSO app settings: The APP Federation Metadata URL can be read here.
rights management
If you previously selected the option " No rights " for alternative rights, you must now activate rights management via edoobox.
Link admin
If you select the Link Admin option, an admin stored in edoobox will be linked to SAML. As soon as this person logs in via SAML, these accounts will be automatically linked. This simplifies the access process and ensures that the correct administration rights are available immediately after logging in via SAML.
Then click on "Add" to add the provider.
Now open the stored provider:
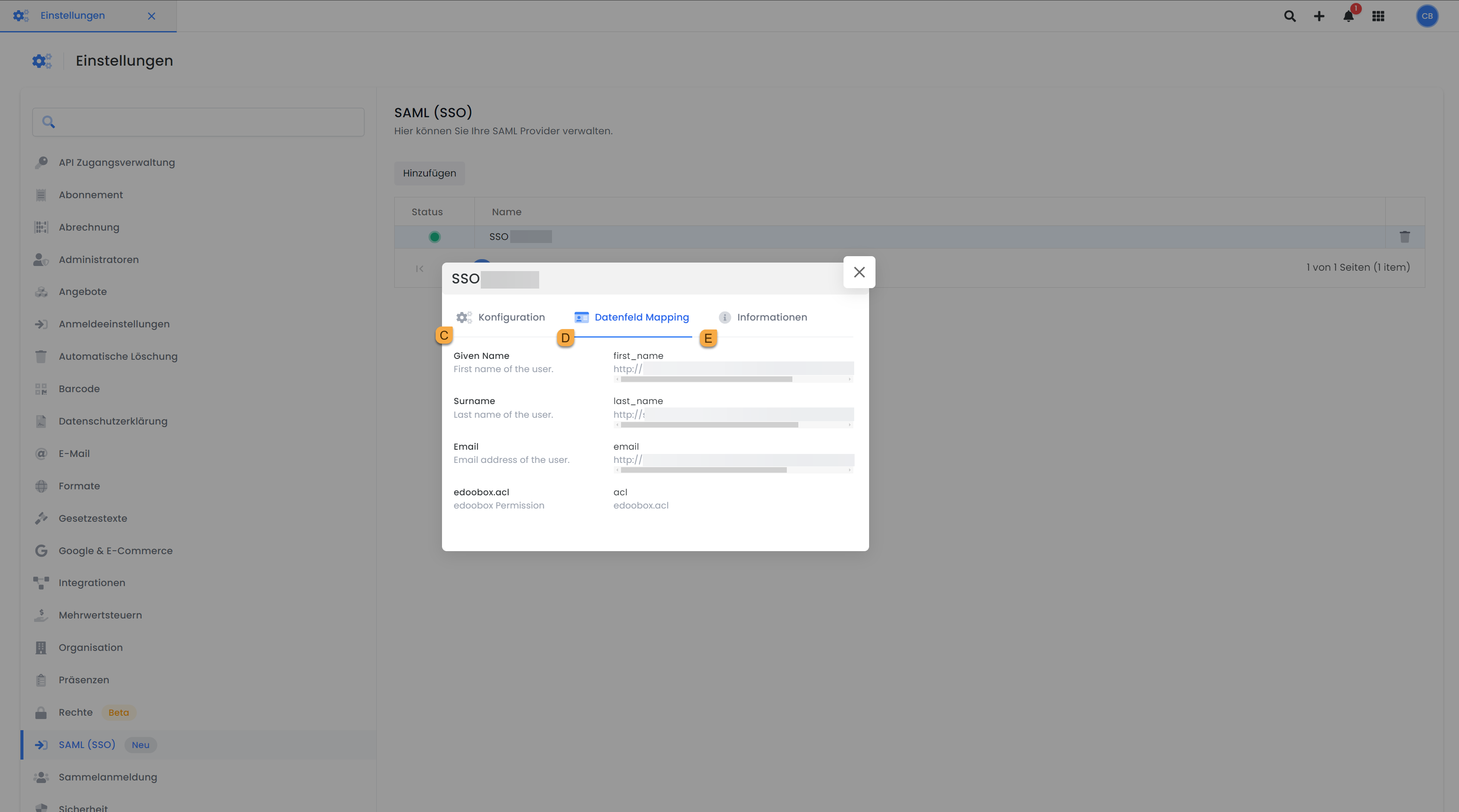
Added provider: Data Mapping
You will receive an overview of the data you previously entered under Configuration C.
Under Data Field Mapping D, first name, last name, email, and ACL rights are mapped automatically. If you want to map additional data fields, you can do so via the API. There you can configure your own mappings.
In the Information E section, you will find details that are extracted directly from the URL. This data cannot be changed unless you delete the provider and set it up again. It is possible to download the information as federationmetadata.xml.
Check whether the login works by logging in at the following URLs:
edoobox V1 login URL: https://app2.edoobox.com/login/sso/IHR-EDOOBOX-KÜRZEL/
edoobox V2 login URL: https://app2.edoobox.com/ed-admin/pages/sso/IHR-EDOOBOX-KÜRZEL/
When you click on the "SSO your company name"login button, you may receive a message informing you that you could not be logged in. If this window appears, you must enter the URL displayed in the window, , as the identifier (entity ID) with your provider (e.g., Azure).
Note: Redirect to SSO
If an administrator is logged in with SSO and logs out or is automatically logged out by edoobox, the logged-out administrator is automatically redirected to the SSO login page and not to the normal login page. For this to work, the administrator must have logged in at least once before.
Related instructions
Keywords for these instructions
SSO ¦ SAML ¦ APP Federation Metadata URL ¦ Provider
